We wrote a blog analogizing vulnerability remediation and Russian Roulette, and then we asked ChatGPT to do the same. Here are the unedited results.
Russian Roulette and Vulnerability Remediation – by trackd.com
I’ve never played russian roulette. My guess is, with the exception of actors in movies, very few have. Most people prefer not to gamble with their lives, even if your odds of surviving the first round are 83% (⅚). But the 83% probability figure is likely to convince many of us to, say, wager $100 in a casino or on a live sports event. An 83% chance of winning is tempting. And what if the odds were a 98% chance of winning? We still wouldn’t bet our lives (well, most of us), but maybe a couple thousand dollars? The kids’ college fund? Everyone has a different tolerance for risk, but a 98% probability of winning I would think gets the attention of most.
As we all know, risk is quantified by multiplying the likelihood of occurrence by the consequence of occurrence. For example, if the likelihood is really high, but the consequence is trivial, the risk is low. The graphic below simplifies a risk calculation to 4 possibilities. For example, as an average (at best) high school wrestler in Pennsylvania, the likelihood of me losing a match was pretty high, but, despite my perception at the time, the consequences of doing so didn’t alter the trajectory of the planet or otherwise impact my life or others in any serious way, so the risk of walking onto the mat was low. Similarly, the risk of betting $50 on the Orioles to win the World Series this year is low, both because it’s unlikely they’ll do so, and because losing $50 won’t make or break the financial fortune of the typical gambler (one hopes).
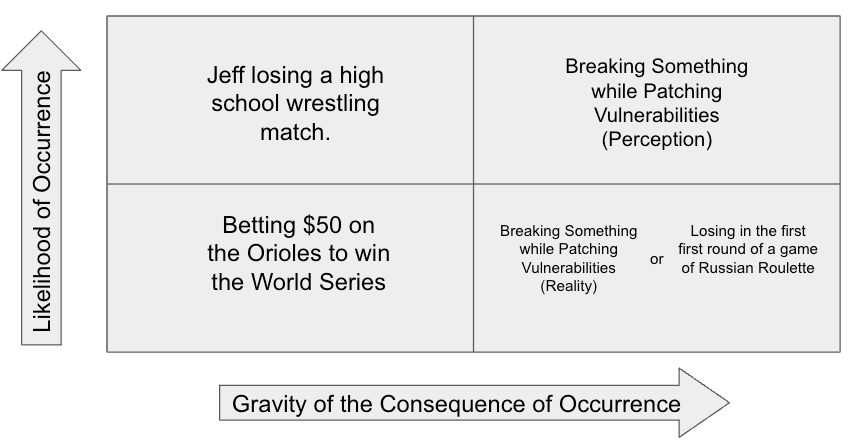
Applying this same risk analysis methodology to patching, however, introduces an interesting complexity: perception. If we surveyed a group of vulnerability remediation practitioners, at least a majority – likely a large percentage of them – would identify the risk elements of causing a disruption while patching to be both highly likely and the consequences to be serious, placing the risk of breaking something firmly in the upper right quadrant of our graphic. Reality and data, however, would take exception with that assessment.
Unlike the patching reality of 10 or 20 years ago, today, less than 98% of patches are rolled back, meaning a small percentage of all applied patches result in serious operational disruptions. So, as depicted in the figure above, the most appropriate place in the quadrant for the risk of breaking something while patching is the bottom right, or the intersection of a low probability of occurrence, but a highly serious consequence. Certainly, even if only 2% of patches are disruptive, that 2% can do some real damage. Indeed, there’s a reason the risk of losing in Russian Roulette is located in the same quadrant as the risk of breaking something during a vulnerability’s remediation. Although it’s unlikely a network disruption resulting from an applied patch will result in the loss of life – some healthcare IT professionals may disagree – taking down a critical enterprise system unexpectedly can be catastrophic.
So even with the knowledge that 98 out of 100 patches are safe to deploy, remediation teams are unlikely to modify their processes to patch more aggressively any more than the average person would change their decision to play Russian Roulette with a gun with 100 chambers and only 2 live bullets. The consequences are simply too serious to take the risk, even with those odds. The only way to change the behavior of remediation practitioners is to give them data that helps them identify the 2 chambers with the live bullets, enabling them to patch accordingly. Otherwise, remediation teams are just, well, playing Russian Roulette with better odds.
Russian Roulette and Vulnerability Remediation – by ChatGPT
Prompt: “write me a 600 word blog on the risk of vulnerability remediation using russian roulette as a metaphor”
In the world of cybersecurity, vulnerability remediation is a critical process that helps to protect computer systems, networks, and applications from malicious attacks. Vulnerabilities can be exploited by attackers to gain access to sensitive information, compromise systems, and cause damage to organizations. Therefore, it is essential to remediate vulnerabilities as quickly as possible. However, the process of vulnerability remediation itself can be risky and lead to unintended consequences if not managed correctly. One way to think about the risks associated with vulnerability remediation is through the metaphor of Russian roulette.
Russian roulette is a game of chance in which players take turns pointing a revolver at their own heads and pulling the trigger. The revolver has a single bullet, and players do not know if the bullet is in the chamber or not. The game is played until someone pulls the trigger and the bullet is fired. In the context of vulnerability remediation, Russian roulette refers to the process of patching vulnerabilities without fully understanding their potential impact on a system. Just like in the game of Russian roulette, patching a vulnerability can lead to unintended consequences and potentially cause a system to fail.
Russian roulette can occur in situations where organizations are under pressure to quickly remediate vulnerabilities, such as after a high-profile data breach or when compliance mandates require swift action. In these cases, organizations may rush to apply patches without fully testing them or understanding the potential consequences. This can create a situation where they are essentially playing a game of chance, hoping that the patches won’t cause further problems.
The risks associated with Russian roulette in vulnerability remediation are significant. Patching one vulnerability could potentially open up new vulnerabilities or cause unintended consequences that could lead to system downtime, data loss, or other security issues. Additionally, organizations may not fully understand the potential impact of a vulnerability patch, leading them to take a “patch and pray” approach. This approach can create a situation where they are essentially playing Russian roulette with their own systems and data.
To avoid the risks associated with Russian roulette in vulnerability remediation, organizations need to take a more thoughtful and measured approach to patching vulnerabilities. This includes:
- Prioritizing vulnerabilities based on their potential impact: Not all vulnerabilities are equal. Some vulnerabilities pose a greater risk to organizations than others. Organizations should prioritize their remediation efforts based on the potential impact of a vulnerability.
- Testing patches in a controlled environment before deployment: Before deploying patches to production systems, organizations should test them in a controlled environment to ensure that they do not cause unintended consequences. This can help to mitigate the risks associated with Russian roulette.
- Having a clear plan for rolling back patches if they cause unexpected issues: In the event that a patch causes unexpected issues, organizations should have a clear plan for rolling back the patch. This can help to minimize the impact of the issue and ensure that the system can quickly return to a stable state.
- Investing in security tools that can help automate vulnerability management processes: Security tools, such as vulnerability scanners and patch management tools, can help to automate vulnerability management processes and reduce the risks associated with Russian roulette.
In conclusion, the risks associated with vulnerability remediation can be significant, and it is essential for organizations to take a measured and thoughtful approach to patching vulnerabilities. Rushing to remediate vulnerabilities without fully understanding their potential impact can be likened to playing Russian roulette. By prioritizing vulnerabilities, testing patches before deployment, having a clear plan for rolling back patches, and investing in security tools, organizations can reduce the risks associated with vulnerability remediation and protect their systems and data from malicious attacks.
