Are the Number of Vulnerability-Originated Breaches Being Underestimated?

…are 90% of all breaches the result of phishing? Or, perhaps more credibly, is it that 90% of all breaches for which the initial access vector is disclosed are the result of phishing?
This Is Why I Founded trackd

Today, we’re releasing something we’re calling AutoPilot (only because we couldn’t think of anything more clever). At first glance, it’s a basic upgrade to our auto-patching rules engine, offering an additional variable for IT operators to account for when determining whether or not to designate a patch for auto-update.
trackd Releases First Ever Vulnerability Remediation Rules Engine that Leverages Historical Patch Disruption Data
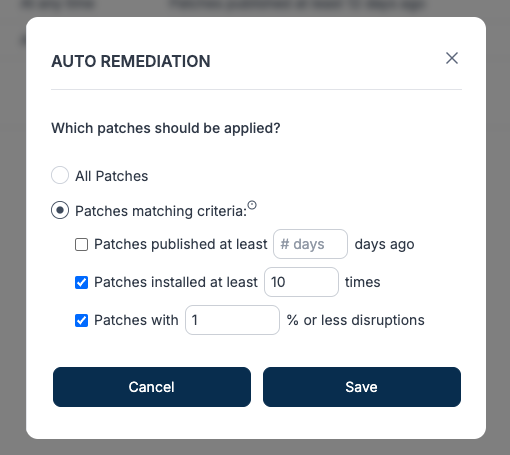
AutoPilot leverages patch disruption data that no other vulnerability scanning or patching product has. When a user applies a patch with trackd’s platform, trackd records whether or not that patch caused a disruption, so trackd has an ever-expanding database of applied patches and their disruption histories.
Wrestling with “Vulnerability Management”

Just as there’s no reason to make weight if you’re not going to wrestle, there’s no reason to scan for and identify vulnerabilities if you’re not going to patch them.
A Faster Horse

Today, those in vulnerability management often create development environments (aka sandboxes) to test whether or not new patches will cause disruptions on their networks…just like they’ve been doing for 3 decades. Which leads to only one conclusion: ARPA-H is funding an effort to build a faster horse.
Why Patches Fail

The psychological source of this particular patch failure, of course, is the omnipresent fear that applying patches will result in a service disruption that will, at a minimum, make for a miserable few hours for IT practitioners, and could result in more serious repercussions. trackd was founded to counter exactly this rational, but largely anachronistic, fear.
How to Patch Vulnerabilities: A Comprehensive Guide

Leaving vulnerabilities unpatched can expose organizations to significant risks. Attackers actively search for known vulnerabilities to exploit, and exploiting unpatched vulnerabilities is a common technique. Such attacks can result in data breaches, financial losses, reputational damage, and legal liabilities.
Why Patches Fail

In this blog series, we’ll look at some of the more mundane – albeit common and operationally-significant – reasons patches fail.
MSP Patch Management: The Delicate Balance Between Operational Risk & Security Risk

The only thing better than learning from your own mistakes is learning from the mistakes of others. At trackd, we have come up with a radically simple but elegant solution to help organizations differentiate between the 98% of patches that are necessary and safe, and the 2% that will have your clients calling you on the weekends.
Providing Cybersecurity to the Underserved, and Building a Business by Doing So

At trackd, our free users are essential to our business plan; we literally can’t deliver the unique solution we’ve designed without them.